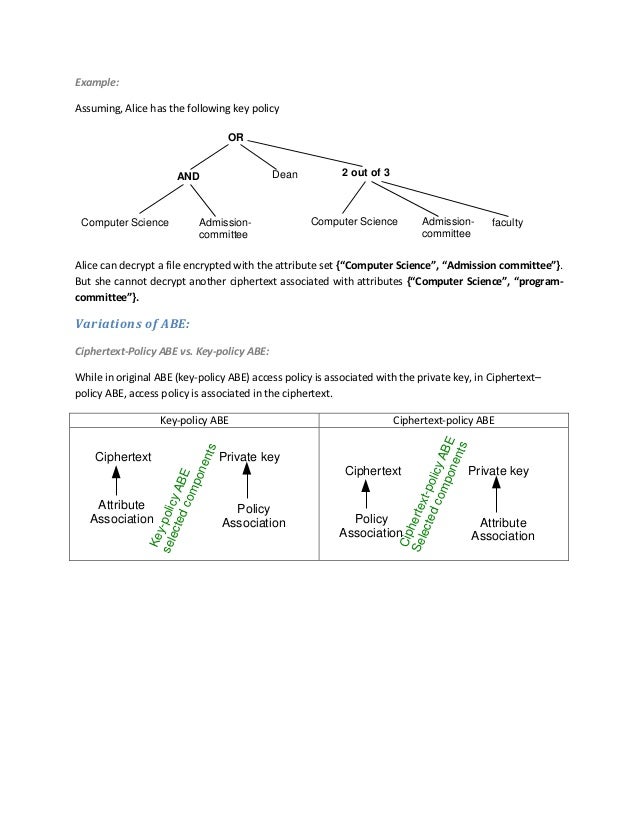
Attribute Based Encryption Tutorial
Start Today and Become an Expert in Days. Expressive access controls.

Attribute Based Encryption For Circuits From Multilinear Youtube
This software is a Java realization for ciphertext-policy attribute based encryption CP-ABE.
Attribute based encryption tutorial. You can get it from the following page. Our scheme allows the data owner to conduct a fine-grained search authorization for a data user. T runs MasterKeyGen gets PK M SK M and publishes PK M Individual setup.
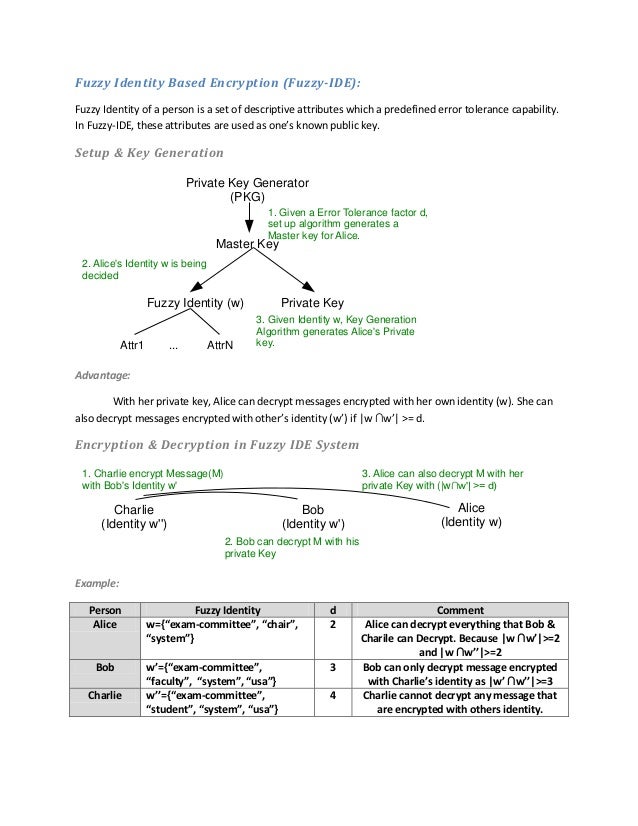
Lattices have allowed us to realize several advanced notions of computation over encrypted data notably fully homomorphic encryption attribute-based encryption as well as fully homomorphic signatures. T runs KeyGenSK M ID A gets SK A and gives SK A to A Encryption. Attribute-based encryption is a kind of algorithm of public key cryptography in which the private key is used to decrypt data is dependent on certain user attributes such as.
EncryptID A PK M m x Decryption. Join Millions of Learners From Around The World Already Learning On Udemy. Decryptx SK M.
It uses encryption based on lightweight attribute-based encryption. To use this software you will need to have the Java Pairing Based Cryptography LibraryjPBC installed jpbc-121 is tested. In this function the message is encrypted and transmitted to several nodes that are quite common in IoT applications.
An attribute-based encryption scheme for any polynomial-time Turing machine and Random Access Machine RAM. A Tutorial Before giving the formal de nitions we describe the key idea behind all RBE construction using a series of strawman constructions so that the readers who are unfamiliar with RBE can build an intuition of how it works and why the key building block hash garbling is needed. In this tutorial we will introduce and derive a simple equation at.
In general the algorithm. SMQTT stands for Secure MQTT. In this paper we present a signcryption scheme called CP_ABSC based on Ciphertext-Policy Attribute Based Encryption CP_ABE 7 to secure the multicast communications in smart grids that require access control data encryption and authentication to ensure message integrity and confidentialityCP_ABSC provides algorithms for key management signcryption and designcryption.
Ad Learn Encryption Online At Your Own Pace. 18 pages published by 2015-04-22 104502. Server stores data in clear.
The main advantage of attribute-based encryption is it uses the broadcast encryption function. Attribute-based encryption ABE is considered a promising technique for cloud storage where multiple accessors may read the same file. This library includes public key encryption schemes identity-based encryption schemes attribute-based encryption schemes digital signatures privacy-preserving signatures commitment schemes zero-knowledge proofs and interactive protocols such as.
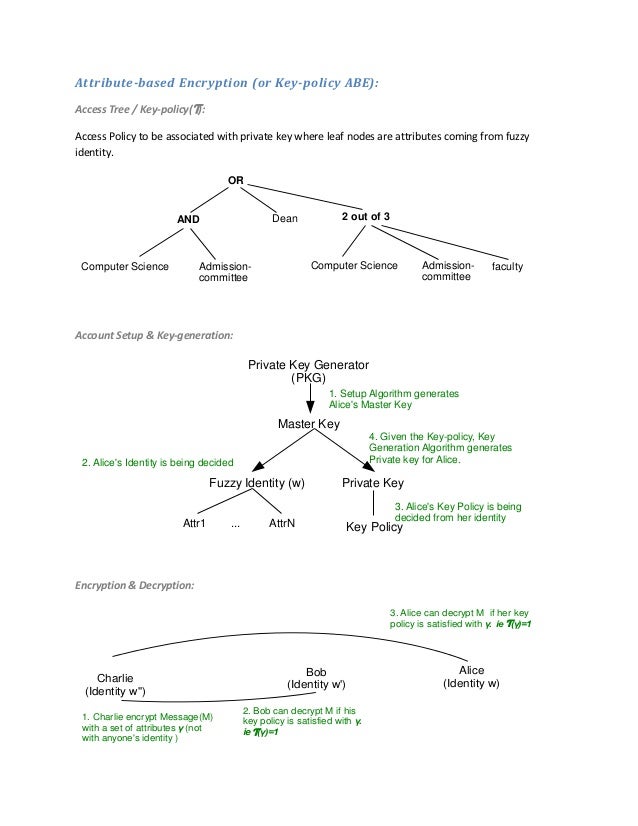
Attribute-Based Encryption 1 Attribute-Based Encryption Brent Waters SRI International 2 Server Mediated Access Control File 1. Join Millions of Learners From Around The World Already Learning On Udemy. Access list John Beth Sue Bob Attributes Computer Science Admissions.
In this paper we propose an attribute-based searchable encryption scheme by leveraging the ciphertext-policy attribute-based encryption technique. 2 Registration Based Encryption. Start Today and Become an Expert in Days.
For storage system with specific personal health record PHR we propose a modified ciphertext-policy attribute-based encryption scheme with expressive and flexible access policy for public domains. This tutorial is intended to propose a framework which bridges NDN architecture with the newly developed crypto-graphic primitives such as attribute-based encryption ABE and specifically discusses the feasibility of coupling NDN and SDN together in solving the trust-roots problem by seamlessly deploying cryptographic infrastructures. Ad Learn Encryption Online At Your Own Pace.
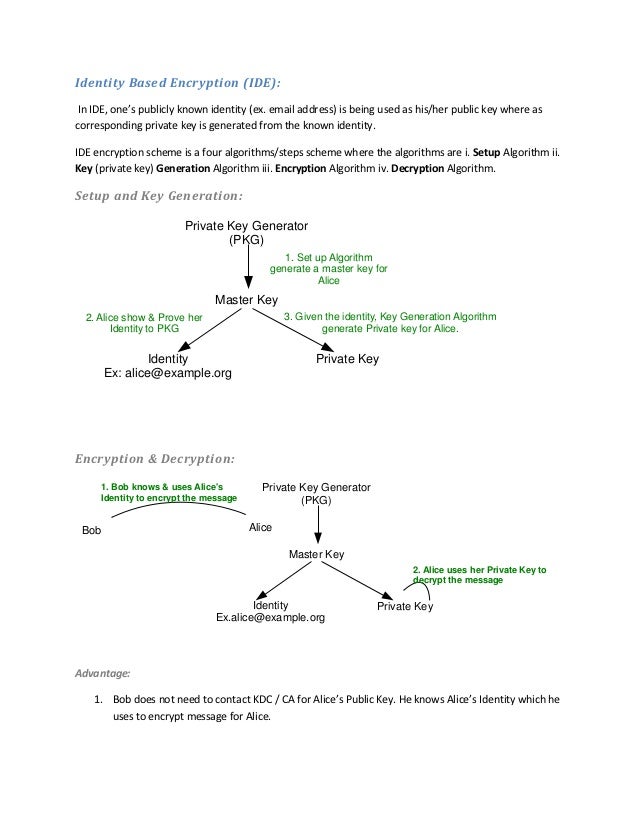
IdentityBased Encryption Master setup. How to Run Turing Machines on Encrypted Data Specifically we show.